Installing/Servicing Since 1981
Call us: 908-428-1130
1-800-5-NOVACOM
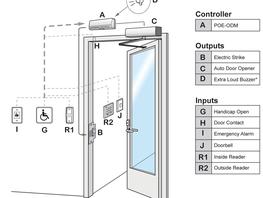
A-IP Ethernet control module uses your data network
C-Elect Auto door opener for door or gates
D-Optional buzzer for annunciation that door is opening
G-Optional ADA compliance for door release
H-Optional Door contract for interface to burglar detection
I-Optional emergency annunciation sounder.
J-Optional Doorbell
R1-Elect inside reader pair to Outside reader-see media
R2-Outside reader paired to inside reader-see media*
What is on this page.
Basics of door control build your Internet Protocol (IP) based door access connections. See Novacom's 5 step program.
IP connection is the same that you connect: phones, computers, Servers, video, burglar/fire detection, & Access Control; a single platform.
Step 1- All sites have data switch(s) that connect computers. Upgrade to Novacom's Internet Protocol Communication Manager (IPCM) switches to have the state of the art platform to connect: Internet, computers, phones, Access Control, video, and WiFi.
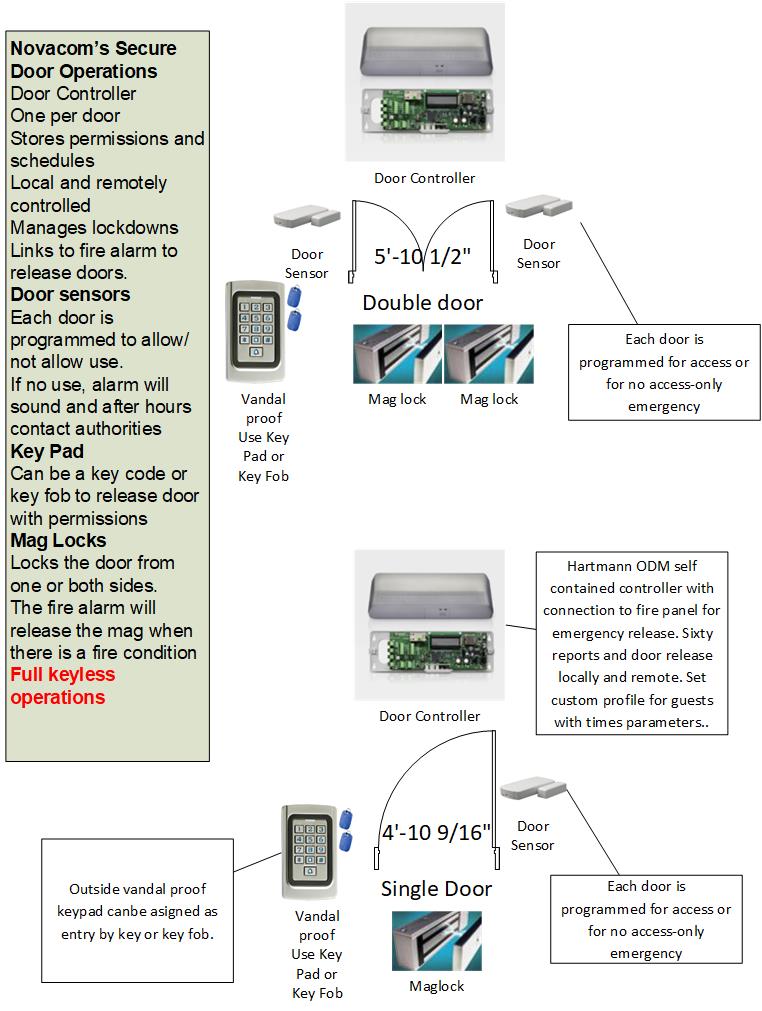
Step 2-Determine the type of door lock device(s) needed.
Step 3-Select: Media card with/without photos, fob, keypad, finger print, and iris (eye) reader.
Step 5-Elect if cameras will synchronize with Access Control. Any door event, door open, is recorded simultaneously with the video image. Simply, view the Access Control event and the video image appears.
Step 4-Select the method to manage the door access; cell/Onsite or Onsite Computer. See AllPlatforms.
Novacom's IP Source = IP Internet + Computers & Printers + WiFi + P Phones+ IP Video + IP Access= Novacom
IP Based self contained door controllers. Each entry point has its own controller networked to unlimited sites and 10,000 controllers.
Keypads, key fobs and card media. Elect photo ID and numeric key reading. Key fobs are most popular.
Cards offer single swipe or dual verification. Encription affords added levels of access credentials needed for high secuity applications
See Magnetic Locks